C60T’s Status Page
C60T’s 3G/4G Page
It is a 3G, Wi-Fi and router device that allows your remote machines and terminals to be connected to the internet via 3G network.
With MOBITEK C60T, you can use your PC in office to access these machines at remote sites:-
MOBITEK C60T is a M2M Wireless Gateway having 3G, Wi-Fi and Router functions in one single device.
To set-up, connect MOBITEK C60T to the PC using the RJ45 via LAN2 port. The sim card is inserted and turned on the power.
The default gateway of MOBITEK C60T is 192.168.1.1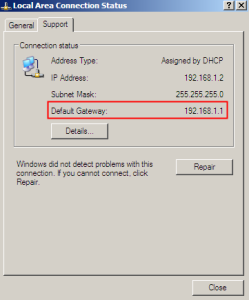
The IP address of MOBITEK C60T is type in the browser to access the administration web page.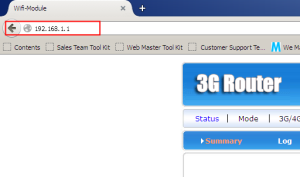
The authentication required the username and password. The “admin” is put on both username and password.
The “Auto select 3G/4G ISP” is unchecked.
The following setting is manually enter values to the TELCO/SIM (Maxis) using:-
Refer table below for list of TELCOs’ 3G Settings:-
If the above table fail to work, then use this table:-
The configuration of MOBITEK C60T is successfully configured and verified by accessed the web page www.mobitek.com.my via 3G network.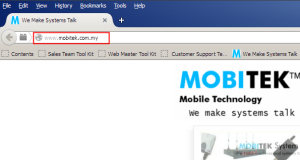
Explanation:
For the Equipment Function, UPNP (Universal Plug and Play) is a set of networking protocols that permits networked devices, such as personal computers, printers, Internet gateways, Wi-Fi access points and mobile devices to seamlessly discover each other’s presence on the network and establish functional network services for data sharing, communications, and entertainment.
There are two options for the remote, disable or enable. If enabling a remote, and enter ‘http://WAN IP:8080′ in your bworser’s address bar, the you can access your device. Figure below as a proof accessed the device.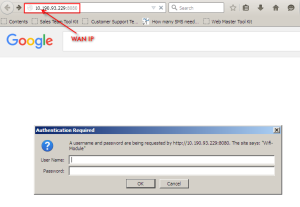 Telnet is a user command and an underlying TCP/IP protocol for accessing remote computers. Through Telnet, an administrator or another user can access someone else’s computer remotely.
Telnet is a user command and an underlying TCP/IP protocol for accessing remote computers. Through Telnet, an administrator or another user can access someone else’s computer remotely.
System Log The system log file contains events that are logged by the operating system components.
(source: https://en.wikipedia.org/wiki/Universal_Plug_and_Play , http://searchnetworking.techtarget.com/definition/Telnet , http://www.webopedia.com/TERM/S/system_log.html)
 Explanation:
Explanation:
Network Time Protocol (NTP) is a networking protocol for clock synchronization between computer systems over packet-switched, variable latency data networks.
(source: https://en.wikipedia.org/wiki/Network_Time_Protocol)
 Explanation:
Explanation:
Backup and Restore functiong for copying and archiving of computer data so it may be used to restore the original after a data loss event.
(source: https://en.wikipedia.org/wiki/Backup)
 Explanation:
Explanation:
Firmware-Upgrade table show the information about the latest software version and the to upgrade the version, just upload the file and begin the upgrade process.
 Explanation:
Explanation:
The restart button is located at admin page and once clicked, the router is restart.
 Explanation:
Explanation:
Factory defaults will reset all settings back to factory defaults if you messed up with all the configurations.
 Explanation:
Explanation:
Admin can change the password at the modify web password. Let say the default password is ‘admin’ and change new password to ‘mobitek’. If the authentication required the password, enter a ‘mobitek’ to access an admin page.
 Explanation:
Explanation:
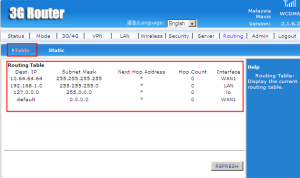
Routing Table above display the information about the current routing table.
The Destinantion IP address is the IP address to which message is sent. Networks using the TCP/IP protocol route messages based on the IP address of the destination.
The subnet mask is a binary pattern that is stored in the client machine, server or router. It is matched with the IP address of a packet to determine which network segment the packet is destined for.
Next hop is a routing term that refers to the next closest router a packet can go through. More specifically, next hop is an IP address entry in a router’s routing table, which specifies the next closest/most optimal router in its routing path.
The hop count refers to the number of intermediate devices (like routers) through which data must pass between source and destination.
(source: http://itlaw.wikia.com/wiki/Destination_IP_address , http://www.pcmag.com/encyclopedia/term/52186/subnet-mask , https://www.techopedia.com/definition/2447/next-hop , https://en.wikipedia.org/wiki/Hop_%28networking%29
Explanation:
Static Routing allow user to define path reaching to another network or host.
 Explanation:
Explanation:
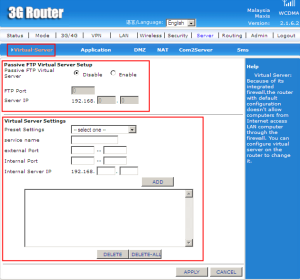
Passive FTP (File Transferring Protocol) virtual server mode is extensively use to solve the issue of the client firewall blocking the FTP server data connection.
Virtual Server setting is a platform to configure virtual server on the router to change due to the router with default configuration does not allow computers fron Internet access LAN computer trhough the firewall.
(source: http://blogs.msdn.com/b/mast/archive/2013/12/13/setting-up-a-passive-ftp-server-in-windows-azure-vm.aspx)
 Explanation:
Explanation:
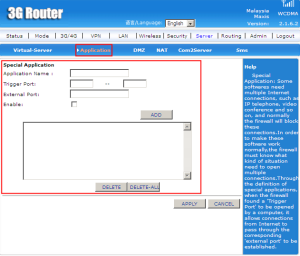
Special Application is defined when the firewall found a ‘Trigger Port’ to be opened by a computer, it allow the connections from Internet to pass through the corresponding external port to be established.
 Explanation:
Explanation:
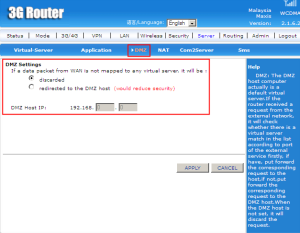
DMZ (Demiliterized Zone) is a physical or logical subnetwork that contains and exposes an organization’s external-facing services to a larger and untrusted network, usually the Internet. The purpose of a DMZ is to add an additional layer of security to an organization’s Local Area Network (LAN).
(source: https://en.wikipedia.org/wiki/DMZ_%28computing%29)
 Explanation:
Explanation:
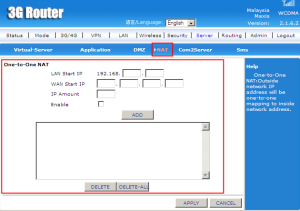
One-to-One NAT (Network Address Translation) is a way tp make systems behind a firewall and configured with private IP addresses appear to have public IP addresses.
(source: http://shorewall.net/NAT.htm)
 Explanation:
Explanation:
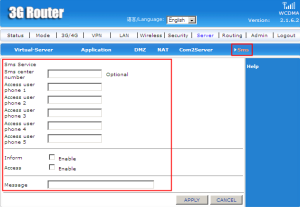
This Sms service is provided by a server to inform the user and messaging a text.
 Explanation:
Explanation:
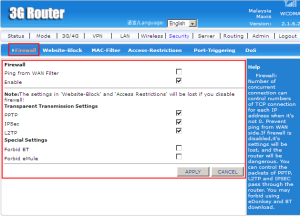
Firewall is a network security system that monitors and controls the incoming and outgoing network traffic based on predetermined security rules.
PPTP (Point-to-Point Tunnelling Protocol) is a method for implementing virtual private networks.
IPSec (Internet Protocol Security) is a protocol suite for securing Internet Protocol (IP) communications by authenticating andd encrypting each IP packet of a communication session.
L2TP (Layer Two Tunnelling Protocol) is an extension of the PPTP used by an Internet Service Provider (ISP) to enable the operation of a virtual private network (VPN) over the Internet.
(source: https://en.wikipedia.org/wiki/Firewall_%28computing%29, https://en.wikipedia.org/wiki/IPsec, http://searchenterprisewan.techtarget.com/definition/Layer-Two-Tunneling-Protocol)
 Explanation:
Explanation:
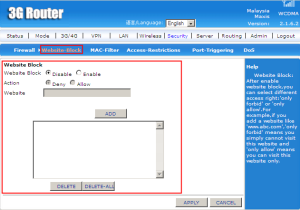
Website-Block is to allow or deny the website to visit. You can set by adding the website for the action of deny or allow.
Explanation:
MAC Filtering refers to a security access control method whereby the 48-bit address assigned to each network card is used to determine access to network. You also can allow or forbid MAC Filtering by adding MAC address in the table.
(source: https://en.wikipedia.org/wiki/MAC_filtering)
 Explanation:
Explanation:
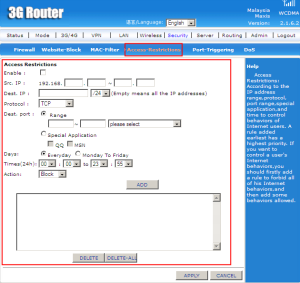
Access Restriction is used to control the behaviors of Internet users.
 Explanation:
Explanation:
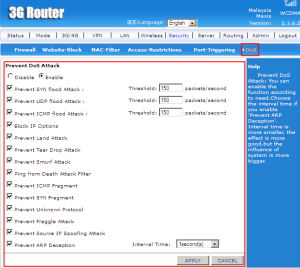
DoS (Denial-of-Service) Attack is an attempt to make a machine or network resources unavailable to its intended users, such as to temporarily on indefinitely interrupt or sespend services of a host connected to the Internet.
SYN flood Attack is a form of DoS attack in which an attacker sends a succession of SYN requests to a target’s system in an attempt to consume enough server resources to make the system unresponsive to legitimate traffic.
A UDP flood Attack is a DoS attack using the User Datagram Protocol (UDP), a sessionless/connectionless computer networking protocol.
An ICMP flood typically occurs when ICMP echo requests overload its victim with so many requests that it expends all its resources responding until it can no longer process valid network traffic.
A LAND (Local Area Network Denial) Attack is a Layer 4 Denial of Service (DoS) attack in which, the attacker sets the source and destination information of a TCP segment to be the same. A vulnerable machine will crash or freeze due to the packet being repeatedly processed by the TCP stack.
A Tear Drop Attack is a DoS attack that involves sending fragmented packets to a target machine. Due to the packets that overlapping one another, the target network device can crash.
A Smurf Attack is an exploitation of the Internet Protocol (IP) broadcast addressing to create a denial of service cause the part of a network become inoperable.
Ping of Death is a DoS attack in which an attacker attempts to crash, destabilize, or freeze the targeted computer or service by sending malformed or oversized packets using a simple ping command.
Internet Control Message Protocol (ICMP) provides error reporting and network probe capabilities. Because ICMP packets contain very short messages, there is no legitimate reason for ICMP packets to be fragmented. If an ICMP packet is so large that it must be fragmented, something is amiss.
A SYN fragment attack floods the target host with SYN packet fragments. The host catches the fragments, waiting for the remaining packets to arrive so it can reassemble them. So, it results the damage to the host’s operating system.
A Fraggle Attack is a denial-of-service (DoS) attack that involves sending a large amount of spoofed UDP traffic to a router’s broadcast address within a network.
ARP stands for Address Resolution Protocol. The principle of ARP cheating, is a kind of IP addresses into physical addresses. ARP specifically to the network layer (IP layer, which is equivalent to the third layer of the OSI) address resolution for the data link layer, MAC layer, which is equivalent to the OSI layer 2) of the MAC address.
(source: https://en.wikipedia.org/wiki/Denial-of-service_attack, https://en.wikipedia.org/wiki/SYN_flood, https://www.juniper.net/techpubs/software/junos-es/junos-es93/junos-es-swconfig-security/understanding-icmp-flood-attacks.html, http://www.imperva.com/Resources/Glossary?term=land_attacks, http://security.radware.com/knowledge-center/DDoSPedia/teardrop-attack/ , searchsecurity.techtarget.com/definition/smurfing , https://www.incapsula.com/ddos/attack-glossary/ping-of-death.html, https://www.juniper.net/techpubs/software/junos-es/junos-es93/junos-es-swconfig-security/understanding-icmp-fragment-protection.html , http://kb.juniper.net/InfoCenter/index?page=content&id=KB4720 , http://security.radware.com/knowledge-center/DDoSPedia/fraggle-attack/ , http://forums.yoosecurity.com/index.php?threads/principle-of-arp-deception.11373/)
 Explanation:
Explanation:
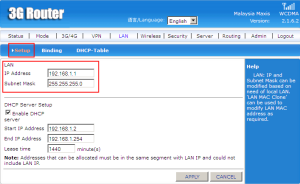
The IP address 192.168.1.1 is assigned on current LAN (Local Area Network) and subnet mask is 255.255.255.0. It can be modified based on need of local LAN.
Explanation:
DHCP servers centrally manage IP addresses and related information and provide it to clients automatically. This allows you to configure client network settings at a server, instead of configuring them on each client computer. So, to make it easier, checked the ‘Enable DHCP’.
On the ‘Start IP Address’ must be set to the LAN port on the same subnet. For default it will start with 192.168.1.2.
On the ‘End IP Address’ the subnet must be same as the LAN port set and the last IP address is 192.168.1.245.
For the ‘Lease time’ the default is 1440 minutes.
(source: https://technet.microsoft.com/en-us/library/cc756865%28v=ws.10%29.aspx, C60T User’s Manual.pdf)
Explanation:
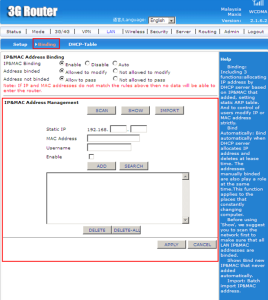
The ‘IP & MAC Binding’ is enable to allow the DHCP server to assign IP addresses according to the added IP & MAC. For the ‘Address binded’ is allowed to control of users modify IP or MAC address strictly.
(source: from C60T User’s Manual.pdf)
 Explanation:
Explanation:
The ‘IP & MAC Address Management’ contain the static IP which is when the device is assigned a static IP address, it does not change. The MAC address is a unique identifier assigned to network interfaces for communications on the physical network segment. The username is the name for the device.
(source: https://www.google.com/?gws_rd=ssl#q=static+ip , https://www.google.com/?gws_rd=ssl#q=mac+address)
Explanation:
The DHCP-Table display all IP address allocated by current DHCP server. So, there are two clients which is DELL-GX280 and android-2f2fbee connected to the C60T.
 Explanation:
Explanation:
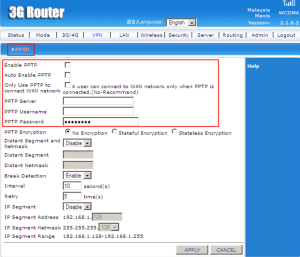
PPTP (Point-to-Point Tunnelling Protocol) is a method for implementing virtual private networks. PPTP uses a control channel over TCP (Trasmission Control Protocol) and a GRE(Generic Routing Encapsulation) tunnel operating to encapsulate PPP packets, the purpose only on implemented security functionality. From the figure above, you can choose to enable or auto enable or only use PPTP to connect WAN network.
(source: https://en.wikipedia.org/wiki/Point-to-Point_Tunneling_Protocol)
 Explanation:
Explanation:
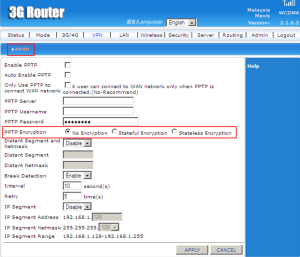
There are three types of encryption which are no encryption, stateful encryption, and stateless encryption. Stateful means the computer or program keeps track of the state on interaction, usually by setting values in a storage field designated for that purpose. Stateless means there is no record of previous interactions and each interactin request has to be handled based entirely on information that comes with it.
(source: http://whatis.techtarget.com/definition/stateless)
 Explanation:
Explanation:
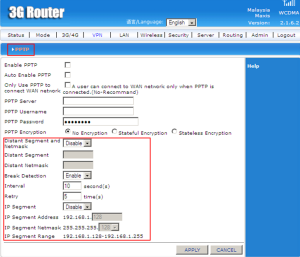
Distant Segment and Netmask can choose to disable or enable. If enable it, the distant segment and distant netmask is need to fill in because as networks grow to increasing number of segments, more network address numbers will be needed as each segment requires an individual number. So, that why we need to put the number. The interval is the time between two points. The retry is the number of attemps if there is any failed. Default IP Segment Range is between 192.168.1.128 until 192.168.1.255. So the IP Segment Address and IP Segment Netmask should be in the range.
(source: http://www.networkcomputing.com/unixworld/tutorial/001.html)
 Explanation:
Explanation:
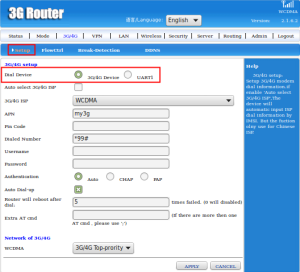
For the Dial Device setup, you can choose either one 3G/4G Device or UART1 (Universal Asynchronous Receiver/Transmitter). UART1 is the microchip with programming that controls a computer’s interface to its attached serial devices.
(source: from http://whatis.techtarget.com/definition/UART-Universal-Asynchronous-Receiver-Transmitter)
Explanation:
You can choose either to auto select 3G/4G ISP or not which is ISP is a Internet Service Provider. It is refers to a company that provides Internet services, including personal and business access to the Internet. An example of ISP is Maxis, Celcom, DIGI and etc.
(source: from http://www.webopedia.com/TERM/I/ISP.html)
Explanation:
There is the lists of 3G/4G ISP that you can select. It is depend on the type of ISP that you used like Maxis, Celcom, DIGI, U-Mobile and etc.
Explanation:
APN stands for Access Point Name which is the name of a gateway between GPRS (General Packet Radio Service), 3g or 4G mobile network. For example cmnet(DIGI), 3gnet(Maxis), celcom3g(Celcom), and my3g(U-Mobile).
(source: from https://en.wikipedia.org/wiki/Access_Point_Name)
Explanation:
The dialed number is depending on the APN. If you are using “cmnet”, the dialed number is “*99# or *98*1#”.
Dialed numbet for “3gnet” is “*99#, for “celcom3g” is “*99***1# and for “my3g” is “*99#”.
(source: from C60T User’s Manual)
Explanation:
The username and password is depends on how you setup the 3G/4G. Usually, the username and password is same and it could be empty.
(source: from C60T User’s Manual)
Explanation:
Just in case, the figure above shows the auto authentication. You also can choose CHAP (Challenge-Handshake Authentication Protocol) which provide protection against reply attacts and provide better security as compared to PAP (Password Authentication Protocol).
(source: from https://en.wikipedia.org/wiki/Challenge-Handshake_Authentication_Protocol)
Explanation:
You can setup number of failed for the router to reboot. For example, if 5 times failed, the router will reboot after dial.
Explanation:
This column is used to put any extra of AT command.
 Explanation:
Explanation:
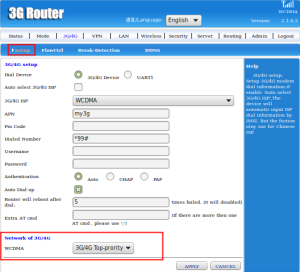
WCDMA stands for Wideband Code Division Multiple Access which is used in the radio leg of both UMTS and HSPA networks. WCDMA can support conventional voice, text, MMS services and can carry data at high speeds, enabling mobile operators to deliver richer mobile multimedia services such as music-on-demand, TV and video straming, and broadband Internet access.
(source: from http://www.gsma.com/aboutus/gsm-technology/3gwcdma)
 Explanation:
Explanation:
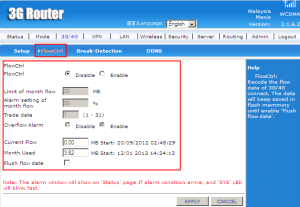
Flow control is recode the flow data of 3G/4G connect. There are two option disable and enable. If enable the flow control, you can set the ‘limit data of month flow (MB)’, ‘alarm setting of month flow’, ‘trade date’. The ‘overflow alarm’ can choose either to enable or disable. If enable, the alarm condition arrive will show on ‘Status’ page and “SYS” LED will blink fast. The current flow show the latest data (MB) and set up the amount of data used in a Month Used. The data will keep saved in flash memory until enable ‘Flush flow date’.
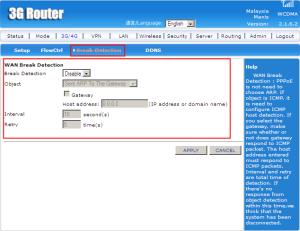 Explanation:
Explanation:
WAN break detection can choose to disable or enable.
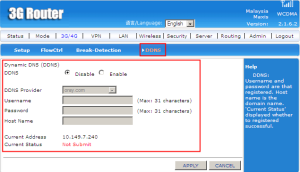 Explanation:
Explanation:
Dynamic DNS allows you to direct your domain or a subdomain to a resource that is behind a gateway that has a dynamically assigned IP address. The current address of 3G Router is 10.149.7.240 (DNS). The webpage opened like the figure above.
(source: https://support.google.com/domains/answer/6147083?hl=en)