 Explanation:
Explanation:
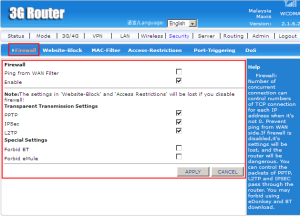
Firewall is a network security system that monitors and controls the incoming and outgoing network traffic based on predetermined security rules.
PPTP (Point-to-Point Tunnelling Protocol) is a method for implementing virtual private networks.
IPSec (Internet Protocol Security) is a protocol suite for securing Internet Protocol (IP) communications by authenticating andd encrypting each IP packet of a communication session.
L2TP (Layer Two Tunnelling Protocol) is an extension of the PPTP used by an Internet Service Provider (ISP) to enable the operation of a virtual private network (VPN) over the Internet.
(source: https://en.wikipedia.org/wiki/Firewall_%28computing%29, https://en.wikipedia.org/wiki/IPsec, http://searchenterprisewan.techtarget.com/definition/Layer-Two-Tunneling-Protocol)
 Explanation:
Explanation:
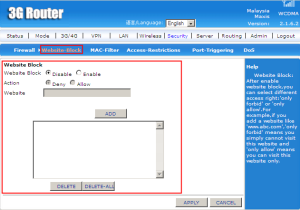
Website-Block is to allow or deny the website to visit. You can set by adding the website for the action of deny or allow.
Explanation:
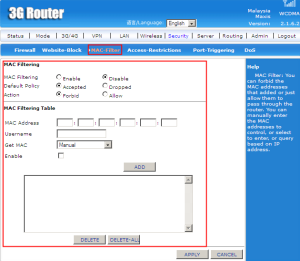
MAC Filtering refers to a security access control method whereby the 48-bit address assigned to each network card is used to determine access to network. You also can allow or forbid MAC Filtering by adding MAC address in the table.
(source: https://en.wikipedia.org/wiki/MAC_filtering)
 Explanation:
Explanation:
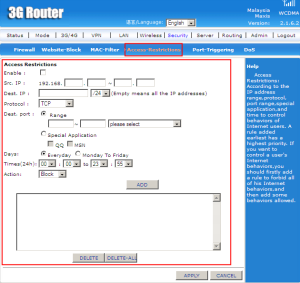
Access Restriction is used to control the behaviors of Internet users.
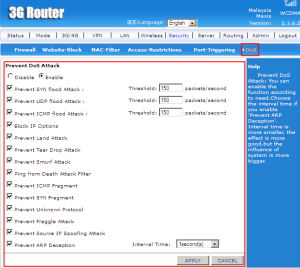 Explanation:
Explanation:
DoS (Denial-of-Service) Attack is an attempt to make a machine or network resources unavailable to its intended users, such as to temporarily on indefinitely interrupt or sespend services of a host connected to the Internet.
SYN flood Attack is a form of DoS attack in which an attacker sends a succession of SYN requests to a target’s system in an attempt to consume enough server resources to make the system unresponsive to legitimate traffic.
A UDP flood Attack is a DoS attack using the User Datagram Protocol (UDP), a sessionless/connectionless computer networking protocol.
An ICMP flood typically occurs when ICMP echo requests overload its victim with so many requests that it expends all its resources responding until it can no longer process valid network traffic.
A LAND (Local Area Network Denial) Attack is a Layer 4 Denial of Service (DoS) attack in which, the attacker sets the source and destination information of a TCP segment to be the same. A vulnerable machine will crash or freeze due to the packet being repeatedly processed by the TCP stack.
A Tear Drop Attack is a DoS attack that involves sending fragmented packets to a target machine. Due to the packets that overlapping one another, the target network device can crash.
A Smurf Attack is an exploitation of the Internet Protocol (IP) broadcast addressing to create a denial of service cause the part of a network become inoperable.
Ping of Death is a DoS attack in which an attacker attempts to crash, destabilize, or freeze the targeted computer or service by sending malformed or oversized packets using a simple ping command.
Internet Control Message Protocol (ICMP) provides error reporting and network probe capabilities. Because ICMP packets contain very short messages, there is no legitimate reason for ICMP packets to be fragmented. If an ICMP packet is so large that it must be fragmented, something is amiss.
A SYN fragment attack floods the target host with SYN packet fragments. The host catches the fragments, waiting for the remaining packets to arrive so it can reassemble them. So, it results the damage to the host’s operating system.
A Fraggle Attack is a denial-of-service (DoS) attack that involves sending a large amount of spoofed UDP traffic to a router’s broadcast address within a network.
ARP stands for Address Resolution Protocol. The principle of ARP cheating, is a kind of IP addresses into physical addresses. ARP specifically to the network layer (IP layer, which is equivalent to the third layer of the OSI) address resolution for the data link layer, MAC layer, which is equivalent to the OSI layer 2) of the MAC address.
(source: https://en.wikipedia.org/wiki/Denial-of-service_attack, https://en.wikipedia.org/wiki/SYN_flood, https://www.juniper.net/techpubs/software/junos-es/junos-es93/junos-es-swconfig-security/understanding-icmp-flood-attacks.html, http://www.imperva.com/Resources/Glossary?term=land_attacks, http://security.radware.com/knowledge-center/DDoSPedia/teardrop-attack/ , searchsecurity.techtarget.com/definition/smurfing , https://www.incapsula.com/ddos/attack-glossary/ping-of-death.html, https://www.juniper.net/techpubs/software/junos-es/junos-es93/junos-es-swconfig-security/understanding-icmp-fragment-protection.html , http://kb.juniper.net/InfoCenter/index?page=content&id=KB4720 , http://security.radware.com/knowledge-center/DDoSPedia/fraggle-attack/ , http://forums.yoosecurity.com/index.php?threads/principle-of-arp-deception.11373/)