 Explanation:
Explanation:
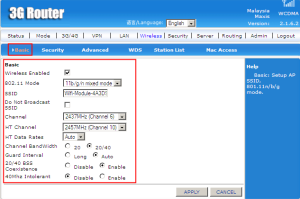
On the basic page of wireless, ‘wireless enable’ can check or uncheck. The ‘802.11’ is the Wi-Fi standards provide the wireless counterpart to Ethernet and the Wi-Fi Alliance certifies products.
The IEEE 802.11 standard have the versions 11b,11g,11n and etc.
The SSID stands for Service Set Idenfier which is the name for wireless local area network. So, the name for C60T wireless is Wifi-Module-4A3D92. It can choose to broadcast SSID or not.
The every channel shows the differences frequency using IEEE 802.11 protocols.
Channel Bandwidth have 20MHz or 40MHz and the purpose is for the actual throughput.
Guard interval is the space between symbol (characters) being transmitted. It is to avoid an interference among them.
The 20/40 BSS Coexistence is enabled due to on the performance of wireless local area network.
(source: http://www.pcmag.com/encyclopedia/term/37204/802-11 , https://en.wikipedia.org/wiki/List_of_WLAN_channels, http://wifijedi.com/2009/02/11/how-stuff-works-short-guard-interval/ , http://ojs.academypublisher.com/index.php/jnw/article/view/03075663)
 Explanation:
Explanation:
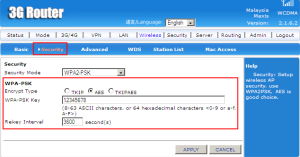
Security is need to secure the network. WPA2-PSK stands for Wi-Fi Protected Access 2 – Pre-Shared Key or Personal, it is a method of securing the network using WPA2 with the use of the optional Pre-Shared Key (PSK) authentication, which was designed for home users without an enterprise authentication server.
(Source: http://www.webopedia.com/TERM/W/WPA2_PSK.html)
WPA-PSK have three types of encrypt. First, TKIP (Temporal Key Intergrity Protocol) is an encryption protocol that was designed to provided secure encryption in wirelss local area network. Second, AES (Advanced Encryption Standard) is a symmetric-key block cipher algorithm and U.S. government standard for secure and classified data encryption and decryption. Lastly, TKIPAES is the combination of TKIP and AES whiich allow you to run mixed system.
WPA-PSK Key need to fill in to secure the wireless network and rekey interval is the the default time of 3600 seconds.
(source: http://searchmobilecomputing.techtarget.com/definition/TKIP, https://www.techopedia.com/definition/1763/advanced-encryption-standard-aes)
 Explanation:
Explanation:
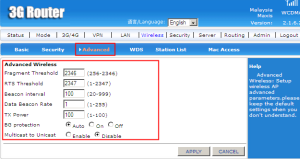
Fragment Threshold is used to specify the maximum size for a data packet before being fragmented into multiple packets and the default size is 2346 bytes.
RTS (Request to Send) Threshold function to control station access to the medium for packet transmission.
Beacon Interval is represent the amount of time between beacon transmission. Before a station enters power save mode, the station needs th beacon interval to know when to wake up to receive the beacon.
Data Beacon Rate is the delivery traffic indication message that specify the data beacon rate between 1-255 and 1 is the default.
TX Power is the strength of the signal that the router produces during the times it is transmitting.
Multicast is a transmission one-to-many broadcast in which wireless forwards all packets. Unicast is one-to-one basis that establishing individual sessions between the transmission server and each client.
(source: https://www.google.com/?gws_rd=ssl#q=RTS+threshold, http://resources.infosecinstitute.com/rts-threshold-configuration-improved-wireless-network-performance/, http://www.manualslib.com/manual/427373/3com-3crwe915075-Airconnect-9150-11n-2-4-Ghz-Poe-Access-Point.html?page=44, https://documentation.meraki.com/MR/Other_Topics/Multicast-Unicast_Conversion)
Explanation:
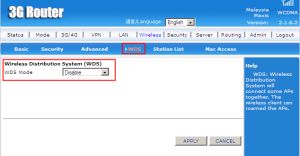
A wireless distribution system (WDS) is a system enabling the wireless interconnection of access points in an IEEE 802.11 network. It allows a wireless network to be expanded using multiple access points without the traditional requirement for a wired backbone to link them.
(source: https://www.google.com/search?q=Wireless+Distribution+System&ie=utf-8&oe=utf-8)
 Explanation:
Explanation:
Current Station List shows all the wireless clients who access the Access Point.
 Explanation:
Explanation:
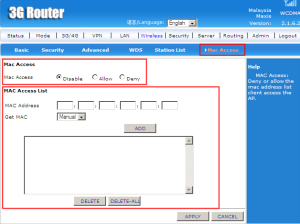
Mac Access can set either to disable, allow, or deny. If allow or deny is choose, enter the mac address on the MAC Access list to allow or deny that mac address of client to access the AP.